A new data center design called the Clos network–based spine-and-leaf architecture was developed to overcome these limitations. This architecture has been proven to deliver the high-bandwidth, low-latency, non-blocked links etc. CLOS topology basically have 2 tier, Spine (Core) and Leaf (Access). Every leaf switch is connected to all Spine switches. The spine layer is the backbone of the network and is responsible for interconnecting all leaf switches.
In the Data Center environment, one of the things we need to consider is, there will be some other devices to provide services like Firewall, Load Balancer to the tenants. The question is, how and where can we placed these service devices in the topology. To answer this question we need to extend our “leaf” definition with “Leaf”, “Border Leaf” and “Service Leaf”. With a simple definition;
Border Leaf is responsible for outside connection like internet. Border Leaf is also responsible from data center interconnect between different data centers.
Border Leaf

Placement of FW to the Border leaf can be used for;
- Inter-VRF traffic (traffic between different tenants)
- External (Internet) traffic
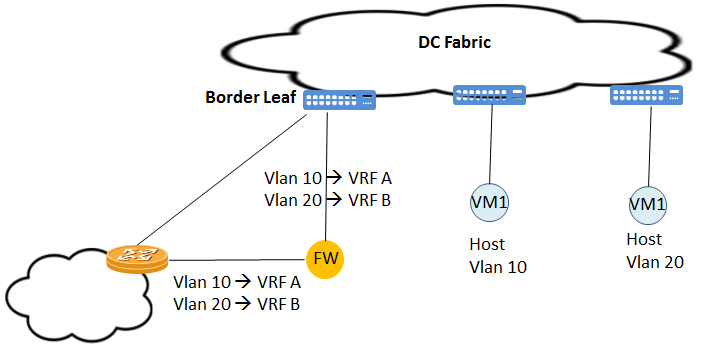
- Transparent Firewall is inserted inline between the Border Leaf and the Edge-Router. VRF-Lite is used between Border Leaf and Edge-Router
- Inside link between the Border Leaf and Firewall is a Dot1Q trunk. Each VLAN has been bind to different VRF which is protected VRF
- Outside link between the Edge Router and Firewall is also a Dot1Q trunk. Each VLAN corresponding to a protected VRF. In the example I gave used the same Vlan ID but it is not must.
- Border Leaf and Edge routers usually use SVIs and per-VRF routing adjacency with eBGP.
- Data traffic for unprotected VRFs, will use direct links between the Border Leaf and Edge Router bypassing the Firewall
- Edge Router performs inter-VRF routing.
The overall performance is related with firewall performance. To increase the performance it is also possible to use different firewalls connected to Border Leaf for different tenant.
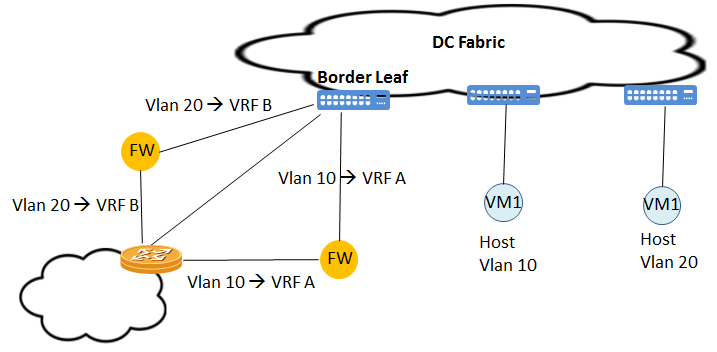
- eBGP peering between Border Lead and Edge Router will be established over transparent mode firewall.
- Local-AS option may be used to prevent route discard caused by as-path.
One of the options is using routed mode for the firewall.

When operating a Firewall in Routed mode, additional configuration will be needed;
- Per-VRF IGP routing adjacency between Border Leaf and Firewall
- Per-VRF IGP routing adjacency between Firewall and Edge Router
Firewall establishes routing adjacencies with both the Border Leaf and the Edge Router.